Innovation Alphabet
Attack Surface
In a nutshell
The term attack surface refers to the part of a system that may be subject to attack or breach by hackers. The smaller that surface is, the easier it will be to protect it. Indeed, the internet is an ocean of deep, dark waters: those who navigate it must be aware that they are exposing themselves to a flood of digital risks. Yet, ironically, we do not need a big boat to shelter us.


How to reduce the Attack Surface
The overall attack surface is much larger than we imagine and consists of a multitude of subjects often difficult to track. For example, in public spaces such as hotels, airports, and coffee shops, hackers can target employees when they access free Wi-Fi. Another method involves targeting employees on their home networks. Or, again, they can attack directly your corporate network, that you put great effort to protect. But hackers can also target your company through other companies you do business with.
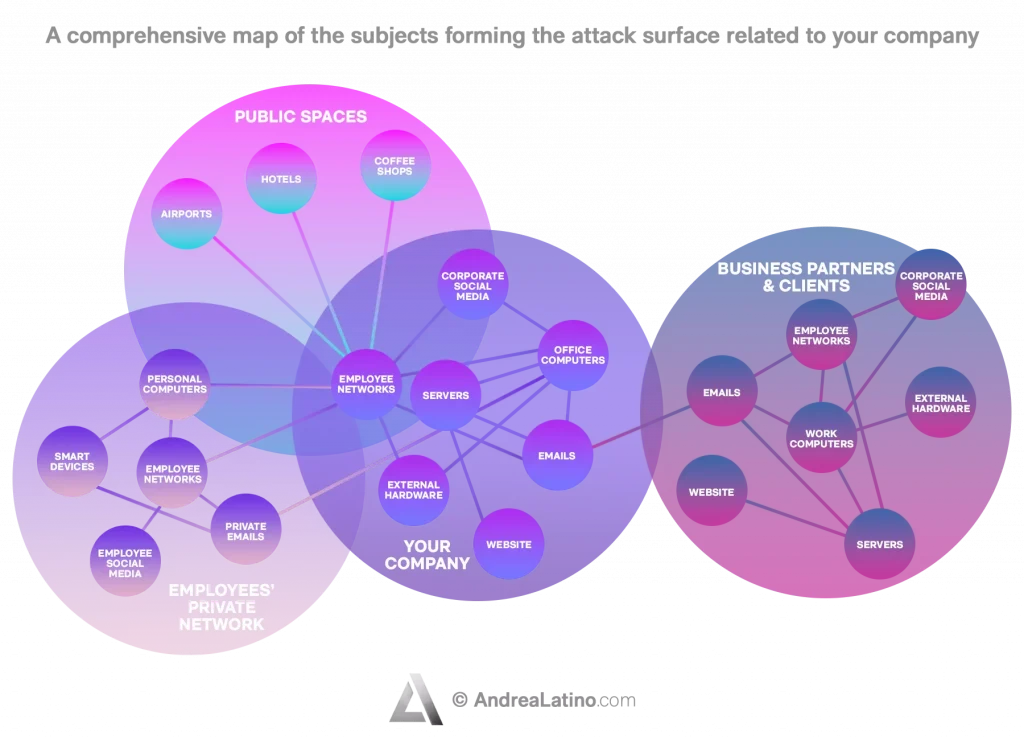
Identify vulnerabilities: You should keep in mind that the attack surface includes all access points and all terminals. But it also includes the paths that data take out of and into applications, along with any codes that protect those paths (passwords and encryptions).
Identify the types of users: Who can access each point in the system? It is not useful to focus on names and badge numbers – it is better to think about the types of users and what they might be looking for.
Conduct a risk evaluation: Which points hold the most users and have the highest level of vulnerability? These are the areas that should be fortified first. There are software programs that can unearth problems that were thought not to exist.
Protect your relationships: How is it possible to understand that you are dealing with a data violation? How does a company act in response to a threat? It may be helpful, if so, to review the company’s IT regulations.
Application Fields
The area of application is almost exclusively IT. Companies should constantly monitor their “attack surfaces” and block potential dangers as quickly as possible. Simultaneously, they should try to minimize the area exposed to hacking to reduce the risk of successful cyber-attacks.
I said “almost”, because attacks can occur as much digitally remotely as by physically accessing the company. That’s why there are cybersecurity agencies capable of testing a company’s cyber and physical security through real espionage activities and James Bond-like tools. A hybrid data-driven approach that uses automated scans and manual verification.
However, such countermeasures may be difficult to implement because they seemingly run counter to the industry’s attempt to expand the digital footprint and embrace new technologies. It should be remembered that the concept of an attack surface includes every input provided by a user, every protocol, every system interface, and all services such as network ports.
Do you have a Public Affairs & Comms challenge to tackle? Let’s face it. Together.
C-levels from these companies (AND MORE) relied on my expertise to overcome thEIR CHALLENGES IN THIS AREA. And you can, too.
Can I help you?Business Functions
• Expanse for the U.S. Federal Agency
The U.S. federal government agency possessed information in data silos between its headquarters, its security operations center, and various field offices, making IT security policies difficult to enforce in a decentralized network on the one hand, and many Intenet-connected assets vulnerable on the other. However, the agency worked with Expanse – a North American company that helps corporate teams monitor (and discover) their Internet-connected assets – to protect numerous points of exposure before hackers could exploit them.
• Microsoft Attack Surface Reduction
Attack Surface Reduction (ASR) are rules that are part of Windows Defender Exploit Guard and that block certain processes and tasks, with the goal of limiting risky behavior and helping protect various organizations. Microsoft knows that applications such as Outlook and Office are the ones most used, and consequently also those most at risk: protecting them must be a priority.
Stay in wonderland
Let me show you how deep the rabbit hole goes.
Check out more of the Innovation Alphabet:
3D Printing
3D Printing
“3D printing” is a process carried out by an electronic device which, instead of resorting to the canonical ink, it molds almost any kind of material: from concrete to living tissue, most usually plastic, but also metal. And the operating principle is similar to that of a traditional printer. The creation of three-dimensional models can lead to the redesign of a company’s production capabilities.
Dive In
5G
5G
5G is the new frontier of cellular telephony. It was designed to improve (or completely replace) previous generations of mobile networks. The 5th generation features lower latency, ensuring flawless performance of business applications and many other digital experiences – thus enabling the new cultural generations to furiously play Fortnite away from home.
Dive In
Advanced Analytics
Advanced Analytics
The term “Advanced Analytics” refers to the ability to autonomously or semi-autonomously analyze data and content to identify correlations, develop analyses, predictions, and recommendations. It is not just a matter of collecting information and then organizing it into watertight compartments: the ultimate goal is to identify a dialogue pattern from a data-driven perspective.
Dive In
Agile
Agile
Agile is an approach to software development designed to respond to change. Teams quickly analyze the context in which they operate, identify uncertainties faced, and figure out how to adapt to always move forward. Interaction between individuals comes before processes and tools; collaboration with the customer is more important than negotiating contracts.
Dive In
Ansoff Matrix
Ansoff Matrix
The Ansoff Matrix is a marketing planning model that arises from the intersection of new and existing products and markets. It derives four possible strategies for expanding the company’s market, which are built around four variables with a changeable factor of risks and possibilities: existing product, new product, existing market, new market.
Dive In
Artificial Intelligence
Artificial Intelligence
Artificial Intelligence is not strictly defined. Basically, it is a computer system able to make decisions in an independent and flexible way. A good AI application can perform everyday tasks better than an average person (e.g., identifying other people from their photos on social media or beating the best chess player). Nothing to fear, then. Unless you are a chess champion.
Dive In
Artificial Scarcity
Artificial Scarcity
We often tend to desire what we cannot have. Or what we are in danger of losing: Artificial Scarcity is a strategy that flaunts a limited number of items that do not correspond to actual availability. The goal is to stimulate the perception in consumers that the stock of items is about to run out and thus create a need based on the “fear of being cut off” or the intention to buy the item in order to resell it at a higher price.
Dive In
Attack Surface
Attack Surface
The term attack surface refers to the part of a system that may be subject to attack or breach by hackers. The smaller that surface is, the easier it will be to protect it. Indeed, the Internet is an ocean of deep, dark waters: those who navigate it must be aware that they are exposing themselves to a flood of digital risks. Yet, ironically, we do not need a big boat to shelter us.
Dive In
Augmented Reality
Augmented Reality
Augmented Reality is an ever-evolving technology that overlays multimedia information on top of our common sensory horizon to gain a deeper understanding of our surroundings. No, it doesn’t allow you to step out of the Matrix dream simulation, nor can it be accessed by swallowing a red pill. But neither is it the disturbing experience of the Playtest episode of Black Mirror.
Dive In
Balanced Scorecard
Balanced Scorecard
In business, as in life, you need balance. The Balanced Scorecard is a holistic tool for strategic management. It offers, in fact, the possibility of assessing corporate performance in its wholeness. An overview that embraces four perspectives: the business/financial side, customers and stakeholders, internal processes, and learning and growth.
Dive In