Innovation Alphabet
Zero-Day Vulnerability
In a nutshell
A zero-day vulnerability indicates a software flaw that developers have known about for “zero days”. As a result, there is no ready security patch to cover the flaw, and hackers can take advantage of it to access data and install malware on the attacked device.


Market Types
Software vulnerabilities give remote access to both stored information and information generated in real time. When a lot of people use the same software one specific vulnerability can be used against millions of people.
This is why hackers have become interested in such vulnerabilities. This has also opened up an ethical debate. Many countries have created public institutions to deal with cybercrime, but they will likely conflict with the interest of their own government to access people’s information in order to prevent crime.
In the end, economic interest always wins, and the vulnerability market thrives under three different directions.
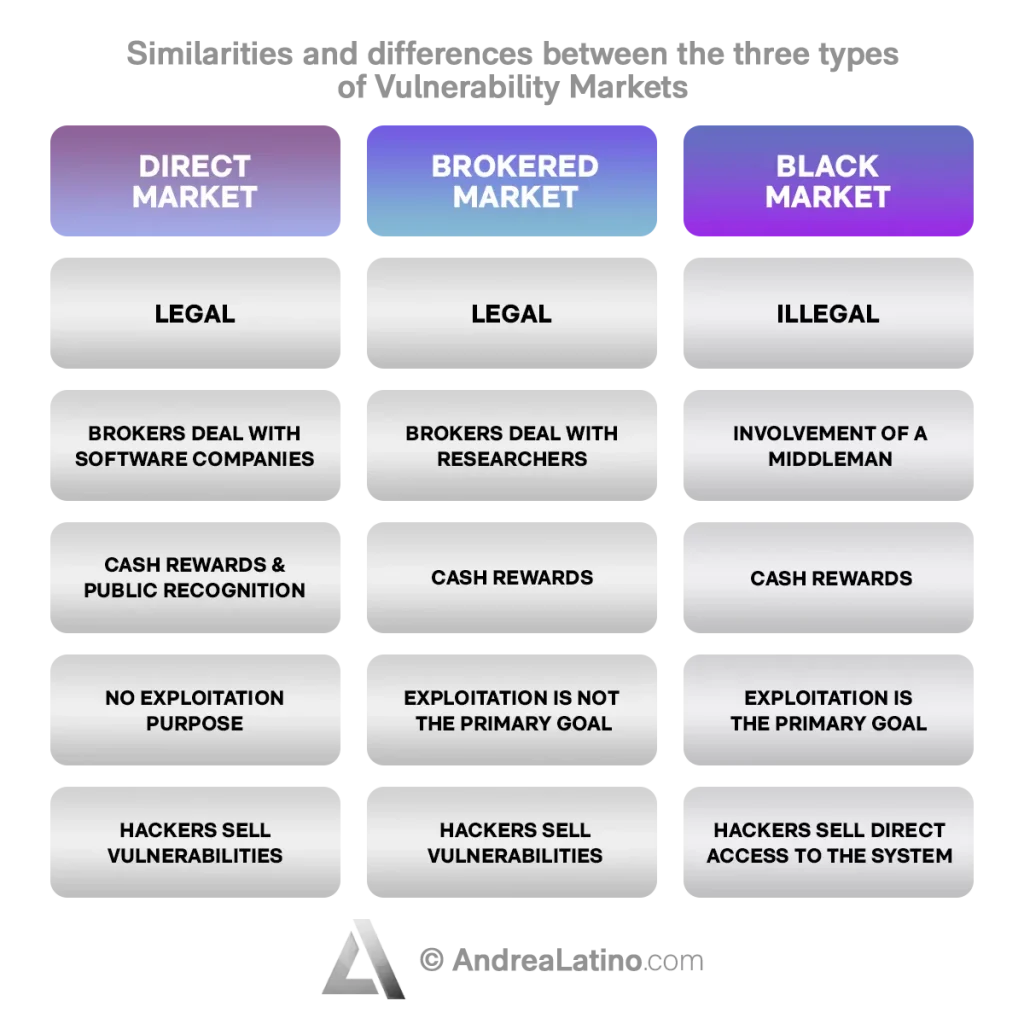
• Direct Market: The Chrome Vulnerability Reward Program is a bug bounty program offered by Google. It provides cash rewards and public recognition to security researchers who invest time and effort to identify new vulnerabilities in Chrome and Chrome OS channels.
• Brokered market: Brokers deal directly with researchers, not with software companies. They validate discovered vulnerabilities and, based on their criticality, pay the discoverers. There are several completely legal sites that validate and pay for vulnerabilities discovered by cyber security researchers. This is a more lucrative type of marketplace than the direct one. It has become popular due to its ease of use, legality, and lucrative nature.
• Black market: This is an illegal market that lives on private or semi-private sites. Sellers offer their zero-days to potential buyers. If the buyers are interested in an exploit (the digital attack corresponding to the vulnerability), the negotiation is carried out by an intermediary whose task is to guarantee the interests of all the actors involved. This is the most profitable type of market, but also the riskiest. It also differentiates itself because instead of selling the identified vulnerability, hackers often sell access to the system directly, preserving the existence of the zero-day.
Do you have a Public Affairs & Comms challenge to tackle? Let’s face it. Together.
C-levels from these companies (AND MORE) relied on my expertise to overcome thEIR CHALLENGES IN THIS AREA. And You can, too.
Can I help you?CASE STUDies
• Stuxnet
This is a virus based on the exploitation of four Windows zero-day vulnerabilities that attacked SCADA systems (related to monitoring and supervising physical systems) and in particular PLCs (Programmable Logic Controllers, computers for managing and controlling industrial processes) of the uranium enrichment plant in Natanz, Iran, sabotaging its nuclear efforts.
• Operation Aurora
In January 2010, a massive cyber-attack from China targeted several U.S. giants including Google, Juniper Networks, and Yahoo, using zero-day vulnerabilities in Internet Explorer and one in Perforce, the code revision software used by Google to manage its codebase. The goal was to steal their trade secrets.
• SecurID hack
In 2011, two-factor authentication titan RSA SecurID suffered an attack that led to the compromise of its network due to a malicious Excel file mistakenly opened by an employee. The breach cost EMC, RSA’s parent company, $66.3 million in investigations, costs to strengthen IT systems and monitor the transactions of more than 30,000 customers.
Stay in wonderland
Let me show you how deep the rabbit hole goes.
Check out more of the Innovation Alphabet:
3D Printing
3D Printing
“3D printing” is a process carried out by an electronic device which, instead of resorting to the canonical ink, it molds almost any kind of material: from concrete to living tissue, most usually plastic, but also metal. And the operating principle is similar to that of a traditional printer. The creation of three-dimensional models can lead to the redesign of a company’s production capabilities.
Dive In
5G
5G
5G is the new frontier of cellular telephony. It was designed to improve (or completely replace) previous generations of mobile networks. The 5th generation features lower latency, ensuring flawless performance of business applications and many other digital experiences – thus enabling the new cultural generations to furiously play Fortnite away from home.
Dive In
Advanced Analytics
Advanced Analytics
The term “Advanced Analytics” refers to the ability to autonomously or semi-autonomously analyze data and content to identify correlations, develop analyses, predictions, and recommendations. It is not just a matter of collecting information and then organizing it into watertight compartments: the ultimate goal is to identify a dialogue pattern from a data-driven perspective.
Dive In
Agile
Agile
Agile is an approach to software development designed to respond to change. Teams quickly analyze the context in which they operate, identify uncertainties faced, and figure out how to adapt to always move forward. Interaction between individuals comes before processes and tools; collaboration with the customer is more important than negotiating contracts.
Dive In
Ansoff Matrix
Ansoff Matrix
The Ansoff Matrix is a marketing planning model that arises from the intersection of new and existing products and markets. It derives four possible strategies for expanding the company’s market, which are built around four variables with a changeable factor of risks and possibilities: existing product, new product, existing market, new market.
Dive In
Artificial Intelligence
Artificial Intelligence
Artificial Intelligence is not strictly defined. Basically, it is a computer system able to make decisions in an independent and flexible way. A good AI application can perform everyday tasks better than an average person (e.g., identifying other people from their photos on social media or beating the best chess player). Nothing to fear, then. Unless you are a chess champion.
Dive In
Artificial Scarcity
Artificial Scarcity
We often tend to desire what we cannot have. Or what we are in danger of losing: Artificial Scarcity is a strategy that flaunts a limited number of items that do not correspond to actual availability. The goal is to stimulate the perception in consumers that the stock of items is about to run out and thus create a need based on the “fear of being cut off” or the intention to buy the item in order to resell it at a higher price.
Dive In
Attack Surface
Attack Surface
The term attack surface refers to the part of a system that may be subject to attack or breach by hackers. The smaller that surface is, the easier it will be to protect it. Indeed, the Internet is an ocean of deep, dark waters: those who navigate it must be aware that they are exposing themselves to a flood of digital risks. Yet, ironically, we do not need a big boat to shelter us.
Dive In
Augmented Reality
Augmented Reality
Augmented Reality is an ever-evolving technology that overlays multimedia information on top of our common sensory horizon to gain a deeper understanding of our surroundings. No, it doesn’t allow you to step out of the Matrix dream simulation, nor can it be accessed by swallowing a red pill. But neither is it the disturbing experience of the Playtest episode of Black Mirror.
Dive In
Balanced Scorecard
Balanced Scorecard
In business, as in life, you need balance. The Balanced Scorecard is a holistic tool for strategic management. It offers, in fact, the possibility of assessing corporate performance in its wholeness. An overview that embraces four perspectives: the business/financial side, customers and stakeholders, internal processes, and learning and growth.
Dive In